Archive for the ‘Revealer Toolkit’ Category
RVT v0.2.1 published
First of all, sorry for the lack of news and updates lately, but RVT is developed with the free and spare time of the members of the team, and I have not had a lot of that in the last months.
RVT v0.2.1 include new features and some little improvements:
- LNK files parsing
- Harlan Carvey, author of the well-known Windows Incident Response blog, has kindly provided us with brilliant Perl code to parse Windows event files (EVT extension). Thus RVT now integrates the script ‘evt’, which can output text versions of the EVT files (script evt generate); it can also generate some stats about each EVT (script evt report). We would like to sincerely thank Harlan for his support and his useful code.
- f-strings: an forensics version of Binutils strings command
- extended shell history
- and all the little changes and corrections published on this blog since v0.2
- updated User Guide
Read The Revealer Toolkit website for more information.
RVT: images scanall: command obsolete
quick note: from SVN revision 70, “images scanall” command is no longer recognized, and is substituted for “images scan <case>”, where case can be a case number or the special word “all”, so “images scan all” is equivalent to the old “images scanall”.
This will speed up the scanning for one case, that will be critical for RWA, although it raises other problems (configuration update time) that will be solved soon.
f-strings, new RVT tool
f-strings, or Forensic Strings, is a new RVT tool that will be incorporated soon to the search engine of RVT.
You know what binutils’ strings command do: extract printable characters from a binary file. Although it supports various character sets (plain ascii, utf8, utf16, in little and big endian), only support one each time you execute it. And it is not very good with mixtures of character sets on the same file.
f-strings extracts sequences of all that seems a printable character out of a binary file, written in plain ASCII, utf8 or utf16 (little endian only). That means that usually will extract more noise than binutils’ strings, but only one execution is needed.
Moreover, f-strings translates special characters to their plain ASCII equivalents. For example, f-strings translates ‘á’, ‘Á’, ‘à’, ‘À’, ‘ä’, etc., to ‘a’. Also translates spanish and catalan special characters ( ‘ñ’ and ‘ç’ to ‘n’ and ‘c’).
Finally, it lowercases all the output.
For example:
$ cat accentuated.txt
el sinvergüenza de José es un ñoño y es del barça$ ./f-strings accentuated.txt
el sinverguenza de jose es un nono y es del barca
f-strings is open source (GNU/GPL v2.0), and can be downloaded from the Revealer Toolkit web page (here).
Here you have the f-strings’ help as printed with ‘f-strings -h‘:
Revealer Tools, forensic strings, 09-2009
USAGE: f-strings [-t] [-n <number> ] [-f]
-t Print the location of the string in base 10
-n Locate & print any sequence of printable characters
of at least characters (default 4)
-h Display this information
f-strings get a file and prints at stdout all printable characters
like binutils' strings function, BUT:
- convert all that 'seems' latin1, UTF-8 and UTF-16, little endian
to plain ASCII
- translates some special characters. For example, accented a's are translated
to the ASCII character 'a'. All vowels, plus spanish and catalan special
characters are translated
- lowercases all printable characters
known issues:
- only one file at each execution
- offset is printed only in base 10, so argument -t do not
accept subarguments, and '-t' is equivalent to '-t d' of
binutils' strings
- \x00 characters are ignored, so in a hard disk full of zeros
with 'Hey ' at the begining and 'Ho' at the end, f-strings will
extract the string 'Hey Ho'
more information at http://code.google.com/p/revealertoolkit/
Enjoy and feedback!
RVT: step by step
Step by step, some ugly parts of the code are being rewritten and getting better. On the last SVN revision, RVT stores on a text file (morgue/case/<case>_cmdLog.txt) a log of some commands executed on that case and their subobjects. Next step will be to work on command dependences.
Also, some automatic reporting is begining to work, although will be greatly redesign in the next months. See RVT commands script report for more information.
Some other little improvements:
- greater command history (greater than one!)
- improvement of lock files (XML configuration, mainly)
- greater readpst verbosity on results
- little sketch for a web interface
RVT: parsing LNK files
support for parsing Microsoft Windows LNK files has been added to RVT. Just execute
RVT > script lnk generate <disk>
and a CSV file on output/lnk will be created with info of all LNK files of the disk (with LNK extension). This command requires other command to be executed before: script files allocfiles or an error will occur. Command dependencies is something we are working on and, I hope, will be solved in version 0.3.
This function depends also on the dumplnk.pl script adapted by Luis Gómez (RVT team member) from the original lnk-parse.pl, by Jacob Cunningham, all GNU/GPL (thanks, open source!), and distributed with RVT (look in the tools folder of the source code, or here)
RVT v0.2 virtual machine
A VMWare virtual machine has been created with a completely functional RVT v0.2 system, folder structure and an example case. This VMWare can easily be used also as a production system.
Due to limitations in Google Code hosting, the VMWare is hosted in sourceforge.net:
- RVT-v0.2.tar.gz
- Authentication: root / 12345 and analyst / 12345
Log in as analyst and run RVT with the command:
$ rvt
RVT v0.2 released
Finally, version 0.2 of the Revealer Toolkit is out. See more information at the project page. Code can be downloaded from:
- http://revealertoolkit.googlecode.com/files/RVT_v0.2.zip
- svn checkout http://revealertoolkit.googlecode.com/svn/branches/RVT-v0.2 RVT-v0.2-read-only
Also, User Guide has been greatly improved with examples and operational guides (see http://revealertoolkit.googlecode.com/files/RVT-userGuide.pdf ).
and finally, a Google Groups newsletter has been created and used for the community to share doubts, ideas and problems ( http://groups.google.com/group/revealertoolkit ). Do not hesitate to contact us!
Stay tunned because important improvements are planned for future versions.
RVT tools: plot_time.pl, plotting your timelines
RVT comes with a bunch of useful tools, not totally related with the forensic framewok, but too little to be published for themselves.
plot_time.pl, located under the RVT/tools folder of the RVT’s svn repository (check it out), it’s a Perl script that plots bar graphs out of files in which each line contains values, being one of them time. It will be handful to represent values on time, or to count the numbers of lines by period of time. This script needs gnuplot 4.2 or greater on your path. Moreover, it uses the powerful Perl module Date::Manip to parse almost every known date format, and can be installed easily from CPAN or APT (apt-get installlibdate-manip-perl).
plot_time.pl works in two modes: representing values as a function of time (mode 1) and representing count of lines as a function of periods of time (integrates the appearance of values over every period defined).
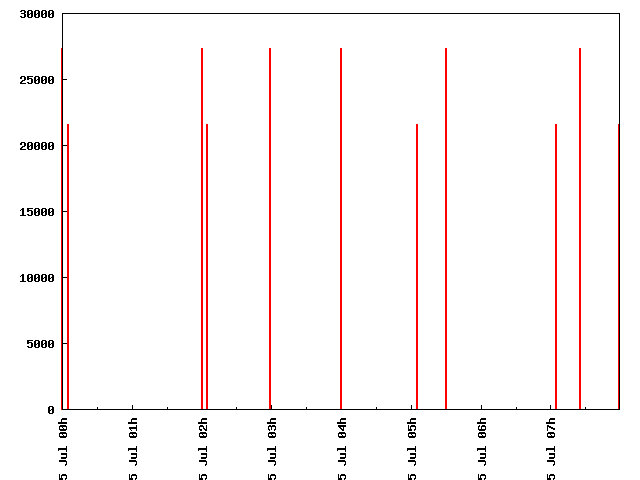
Mode 1. Let’s be itimeline-02.csv a timeline generated with RVT, and let’s imagine that we want to represent graphically the size of the files, as a function of time, on July 5th 2008. We execute the following command:
perl plot_time.pl -interval=’20080705 + 1 day’ -tf 1 -vf 2 itimeline-02.csv
Where ‘tf’ option marks that the first field is the ‘time field’, and ‘vf’ option establishes that the value to be plotted is the second (file size). The following graph is generated:
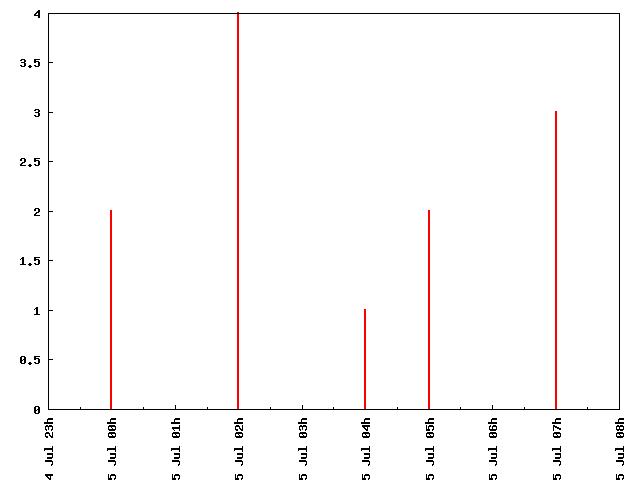
Mode 2. This mode is activated with the ‘-sum’ option, and the period is established with ‘-period’ option, with anything that Date::Manip can understand (‘day’, ‘hour’, …). So, executing the following command on the same data:
perl plot_time.pl -interval=’20080705 + 1 day’ -tf 1 -sum -period=’hour’ itimeline-02.csv
generates the following graph:
Also:
- you can pipe your filtered timelines into plot_time.pl ( f.ex.: grep -i ‘myfile.png’ itimeline-02.csv | perl plot_time.pl … )
- plot_time.pl skips comment lines, and also it can skip a number of lines with ‘-skiplines’ option
- plot_time.pl will ignore lines that match a regular expression when option ‘-excluderegexpr’ is used
- see plot_time.pl –help for more info
We are now planning some new features on plot_time.pl, so stay tunned!
RVT: support for F-Response
last revision of RVT contains a little, tiny, (it’s true, i swear!) change for making RVT directly functional with F-Response. However, the process of installing a new f-response generated device it’s manual. Follow the next steps in order to add remote f-response devices your Revealer morgue:
- assign one, or more, iscsi nodes generated with f-response to linux devices. Documentation on open-iscsi commands are found elsewhere
- assigned devices can be seen with the following open-iscsi command:
iscsiadm -m session -P 3
- now, on your morgue/images/<case> directory, create a symbolic link to each of the devices, with the right RVT nomenclature (<case>-<device>-<disk>.dd). Check the permissions!
# ln -s /dev/sdX 100xxx-yy-z.dd
- run RVT, scan your morgue and use all the functions at convinience!
RVT> images scanall
Feedback if you find problems!
RVT: libpst support
RVT v0.2 will support Microsoft Outlook PST parse support through this command:
- script mail parsepsts <partition>
that extracts all the contents of all PST’s on that partition on output/mail morgue folder